The cybersecurity industry is experiencing unprecedented growth, with global spending expected to reach $314.28 billion by 2028 (Source). But here’s the problem—many security companies are invisible where it matters most: search engines.
When I worked with a Canadian managed service provider specializing in cybersecurity solutions, we achieved 15x keyword growth by strategically positioning their MDR, UTM, and firewall offerings for different buyer personas. The difference? A systematic approach to cybersecurity SEO that addressed both technical implementation and industry-specific optimization challenges.
This isn’t just about ranking higher. It’s about connecting with the right prospects when they’re actively searching for security solutions.
The Reality of Cybersecurity SEO in 2025
The cybersecurity market presents unique SEO challenges that generic marketing advice can’t solve:
Market Competition: In a recent Gartner survey, 80% of organizations said they plan to increase their spending on information security in 2024, creating intense competition for search visibility (Source).
Trust Requirements: Search engines care that a website is secure and this is reflected in its ranking. The more secure the website, the higher it will rank (Source).
Technical Complexity: Cybersecurity buyers require detailed, technical content that demonstrates expertise while remaining accessible to decision-makers.
Buyer Journey Length: Enterprise security purchases involve extended evaluation periods, demanding sustained SEO presence across multiple touchpoints.
Why Traditional SEO Falls Short for Security Companies
Generic SEO strategies miss critical elements unique to cybersecurity marketing:
- Compliance considerations that affect content strategy
- Technical validation requirements for credibility
- Multi-stakeholder decision processes requiring different content approaches
- Regulatory landscape changes affecting keyword relevance
When I managed SEO for a Canadian cybersecurity MSP, we achieved 15x keyword growth by creating solution-specific landing pages for MDR, UTM, and next-generation firewalls—each targeting distinct buyer personas from CISOs to SMB owners. The complete methodology is documented in our MSP SEO case study.
Core Pillars of Effective Cybersecurity SEO
Technical Foundation
Google favours HTTPS protocol, which enhances security by encrypting the connection between the server and the browser (Source). For cybersecurity companies, this isn’t optional—it’s a credibility requirement.
Security-First Technical SEO Elements:
- HTTPS implementation with proper SSL certificates
- Website architecture that demonstrates security best practices
- Page speed optimization without compromising security protocols
- Mobile responsiveness for security-conscious mobile users
Content Strategy Alignment
85% of cybersecurity professionals attribute the increase in cyberattacks to the use of generative AI by bad actors (Source). Your content strategy must reflect current threat landscapes while addressing prospect pain points.
Industry-Specific Content Requirements:
- Technical depth that satisfies IT professionals
- Executive-level summaries for C-suite decision makers
- Compliance-focused content for regulatory requirements
- Threat landscape updates maintaining content freshness
Buyer-Persona-Specific Optimization
Different cybersecurity solutions require different content approaches based on buyer personas:
MDR Services: Target CISOs and IT heads with content emphasizing proactive threat detection, 24/7 SOC monitoring, and incident response capabilities. These buyers research compliance-heavy topics and advanced threat intelligence.
UTM Solutions: Focus on SMB owners and IT managers who need cost-efficient security bundles. Content should highlight consolidation benefits—firewall, intrusion prevention, antivirus, and content filtering in one solution.
Next-Generation Firewalls: Appeal to mid-market IT teams and enterprise architects with technical content about packet inspection, zero-trust architecture, and cloud/application visibility.
Authority Building
In cybersecurity, authority isn’t just about backlinks—it’s about demonstrating legitimate expertise in a field where trust is paramount.
The Complete Implementation Framework
Our systematic approach covers ten critical areas of cybersecurity SEO implementation. Each represents a distinct optimization opportunity that compounds with others to drive meaningful results.
Strategic Website Architecture
Your cybersecurity website structure should reflect how prospects think about security solutions, not how your internal teams organize services.
How to Structure Your Cybersecurity Website for Maximum Organic Visibility
Most security websites organize content around internal departmental structures. But prospects search by problem, threat type, or compliance requirement. This fundamental mismatch costs visibility and conversions.
Schema Markup Implementation Guide for Cybersecurity Service Pages
Generic schema markup misses opportunities to highlight security certifications, compliance standards, and service specifics that influence cybersecurity purchase decisions.
Keyword Research Framework for B2B Cybersecurity Companies
Standard keyword tools often miss the nuanced search patterns of security decision-makers. Our framework identifies high-intent, lower-competition terms that drive qualified traffic.
Technical SEO Audit Checklist for SaaS Security Platforms
SaaS security platforms face unique technical challenges including API documentation indexing, feature page optimization, and integration-focused content structure.
Local SEO Strategy for Regional MSPs and Cybersecurity Consultants
Regional cybersecurity providers can dominate local markets with targeted location-based optimization. This strategy drove significant results for our Canadian clients.
Content Silo Architecture for Multi-Service Cybersecurity Providers
In my experience with cybersecurity MSPs, strategic content silos can drive significant traffic increases by organizing MDR, UTM, and firewall content into logical, search-engine-friendly structures that guide prospects through different service evaluations.
Mobile Optimization Best Practices for Cybersecurity Websites
With the increasing use of smartphones and tablets, optimizing your website for mobile responsiveness is crucial (Source). Security decision-makers increasingly research solutions on mobile devices.
Internal Linking Strategy for Complex Cybersecurity Service Offerings
Complex service portfolios require sophisticated internal linking to guide prospects through evaluation journeys while maximizing page authority distribution.
Conversion Rate Optimization for High-Stakes Security Service Landing Pages
Security purchases involve significant risk assessment. Your landing pages must address trust concerns while driving conversions through strategic optimization.
Page Load Speed Optimization for Security Software Platforms
Implementing optimization techniques such as image compression, browser caching, and minification of CSS and JavaScript files can help improve site speed without compromising security protocols (Source).
Measuring Success in Cybersecurity SEO
Success metrics for cybersecurity SEO extend beyond traditional traffic and ranking measurements. Based on my experience with multiple security companies, here’s what actually matters:
| Traditional Metrics | Cybersecurity-Specific Metrics |
|---|---|
| Organic traffic | Security-qualified lead (SQL) generation rates |
| Keyword rankings | Content engagement depth on technical resources |
| Bounce rate | Certification and compliance content performance |
| Page views | Multi-session buyer journey completion |
Authority Metrics That Matter:
- Mentions in security industry publications
- Speaking engagement requests from content performance
- Technical content sharing within security communities
- Backlinks from authoritative security sources
Industry-Specific Implementation Considerations
Compliance Content Strategy
HIPAA and PCI-DSS compliance requirements create significant SEO opportunities. In my work with Canadian cybersecurity MSPs, compliance-focused content performed exceptionally well because buyers in retail, manufacturing, hospitality, and education sectors expect these certifications as default requirements.
Strategic Approach:
- Top-funnel: Educational content about compliance requirements by industry
- Mid-funnel: “HIPAA-compliant MDR solutions” and “PCI-DSS firewall comparisons”
- Bottom-funnel: Solution-specific landing pages highlighting built-in compliance features
Industries like healthcare, retail, and hospitality actively search for compliance-specific cybersecurity solutions, creating high-intent keyword opportunities with lower competition.
Threat Landscape Content
The second quarter of 2024 saw a 30% increase in cyberattacks compared to Q2 2023 (Source). Your content strategy must reflect current threat patterns while providing evergreen value.
Technology Integration Focus
By 2025, 50% of organizations will be using MDR services (Source). Content must address emerging technology adoption patterns in security operations.
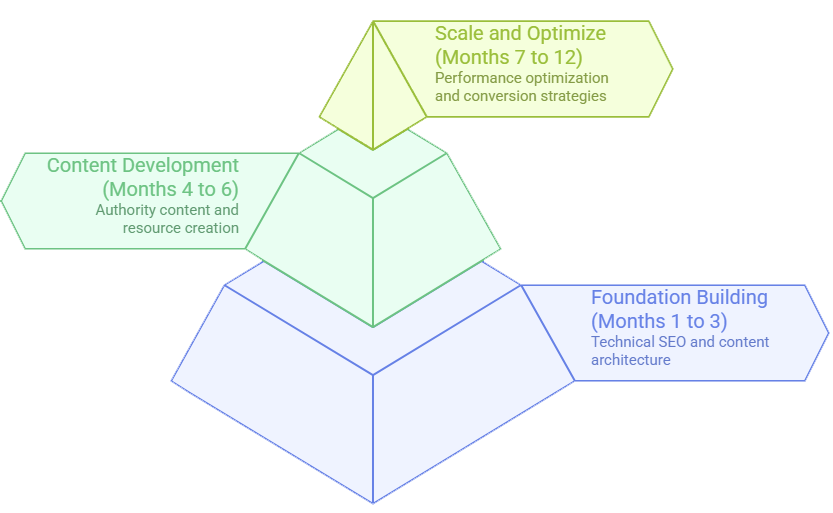
Implementation Timeline and Expectations
Based on our experience across multiple cybersecurity implementations:
| Phase | Duration | Key Activities | Expected Outcomes |
|---|---|---|---|
| Foundation Building | Months 1-3 | Technical SEO implementation, Content architecture development, Initial keyword targeting | 25-40% improvement in technical scores |
| Content Development | Months 4-6 | Authority-building content creation, Technical resource development, Industry-specific optimization | 2-3x increase in qualified traffic |
| Scale and Optimize | Months 7-12 | Performance optimization, Advanced content strategies, Conversion rate improvements | 5-10x improvement in lead quality |
Cybersecurity SEO typically shows accelerated results due to lower content competition in technical niches.
SEO Growth Strategy Pyramid
Getting Started with Cybersecurity SEO
The cybersecurity industry rewards thorough, technical approaches to SEO implementation. Generic marketing tactics fail because they don’t address the unique requirements of security buyers or the technical complexity of cybersecurity solutions. For insights into AI-driven SEO trends that are reshaping how security companies approach search marketing, explore our comprehensive AI SEO statistics analysis.
Success requires combining traditional SEO principles with industry-specific optimization strategies. The framework outlined above provides a systematic approach to building search visibility that drives qualified cybersecurity leads.
Start with technical foundation elements, then build content authority through strategic topic coverage. The companies that dominate cybersecurity search results understand that SEO in this industry is about demonstrating expertise as much as optimizing for algorithms.
Ready to implement these strategies for your cybersecurity company? The framework outlined above provides a systematic approach to building search visibility that drives qualified cybersecurity leads.
Start with technical foundation elements, then build content authority through strategic topic coverage. The companies that dominate cybersecurity search results understand that SEO in this industry is about demonstrating expertise as much as optimizing for algorithms.